22 KiB
22 KiB
- #CT213 - Computer Systems & Organisation
- Previous Topic: Programming Models
- Next Topic: Process Management
- Relevant Slides:
id:: 6326480d-27b6-4d5f-a1d4-5c446ceef351
-
Types of Software
- What is Application Software? #card
card-last-interval:: 23.43
card-repeats:: 4
card-ease-factor:: 2.42
card-next-schedule:: 2022-12-08T06:02:33.036Z
card-last-reviewed:: 2022-11-14T20:02:33.036Z
card-last-score:: 5
- Application Software is a computer program designed to perform a group of coordinated functions for the benefit of the user.
- It is designed solve a specific problem.
- What is System Software? #card
card-last-interval:: 31.05
card-repeats:: 4
card-ease-factor:: 2.56
card-next-schedule:: 2022-12-15T21:10:52.302Z
card-last-reviewed:: 2022-11-14T20:10:52.302Z
card-last-score:: 3
- System Software is a program dedicated to ^^managing the computer.^^
- It provides a platform to other software & a general programming environment.
- There are two main types of system software:
- Operating System
- Utility Software
- What is the Operating System (OS)? #card
card-last-interval:: 29.99
card-repeats:: 4
card-ease-factor:: 2.56
card-next-schedule:: 2022-12-14T19:04:40.695Z
card-last-reviewed:: 2022-11-14T20:04:40.696Z
card-last-score:: 5
- The Operating System provides functions used by the application software.
- It provides the mechanisms for application software to share the hardware in an orderly fashion to:
- Increase the overall performance by allowing different application software to use different parts of the computer at the same time.
- Decrease the time to execute a collection of programs and, again, increase the overall performance
- The OS interacts directly with the hardware to provide an interface to other system software and with application software whenever the application software wants to use the system's resources.
- The OS is application-domain independent, provides resource abstraction, and provides resources sharing through strict resource management policies.
- What is Utility Software? #card
card-last-interval:: 29.99
card-repeats:: 4
card-ease-factor:: 2.56
card-next-schedule:: 2022-12-14T19:04:31.529Z
card-last-reviewed:: 2022-11-14T20:04:31.529Z
card-last-score:: 5
- Utility Software is system software designed to help analyse, configure, optimise, or maintain a computer.
- Examples include data compression, disk cleaners, disk defragmentation, registry cleaners, or system monitors.
- What is Application Software? #card
card-last-interval:: 23.43
card-repeats:: 4
card-ease-factor:: 2.42
card-next-schedule:: 2022-12-08T06:02:33.036Z
card-last-reviewed:: 2022-11-14T20:02:33.036Z
card-last-score:: 5
-
Resources
collapsed:: true- What are Resources? #card
card-last-interval:: -1
card-repeats:: 1
card-ease-factor:: 2.46
card-next-schedule:: 2022-11-15T00:00:00.000Z
card-last-reviewed:: 2022-11-14T16:28:34.225Z
card-last-score:: 1
- Different hardware components that a program may access are referred to as resources.
- Any particular resource, such as a hard disk, has a generic interface that defines how the programmer can make the resource perform a desired operation.
- What is Resource Abstraction? #card
card-last-interval:: 19.01
card-repeats:: 4
card-ease-factor:: 2.18
card-next-schedule:: 2022-12-03T20:01:30.272Z
card-last-reviewed:: 2022-11-14T20:01:30.272Z
card-last-score:: 5
- Resource Abstraction is done by providing an ^^abstract model of the operation of the hardware components.^^
- Abstraction generalises the hardware behaviour but ^^restricts its flexibility.^^
- With abstraction, certain operations become easy to perform, while others may become ^^impossible^^, such as specific hardware control.
- An abstraction can be made to be much simpler than the actual resource interface.
- Simpler resources can be abstracted to a ^^common abstract resource interface.^^
-
Resource Sharing
- Abstract & physical resources can be shared among a set of concurrently executing programs.
- What is Space Multiplex Sharing? #card
card-last-interval:: -1
card-repeats:: 1
card-ease-factor:: 2.22
card-next-schedule:: 2022-11-19T00:00:00.000Z
card-last-reviewed:: 2022-11-18T18:33:28.408Z
card-last-score:: 1
- Space Multiplex Sharing is when resources can be divided into two or more distinct units of the resource that can be used independently.
- E.g., Memory, HDD.
- Space Multiplex Sharing is when resources can be divided into two or more distinct units of the resource that can be used independently.
- What is Time Multiplex Sharing? #card
card-last-interval:: 0.79
card-repeats:: 2
card-ease-factor:: 2.36
card-next-schedule:: 2022-11-15T10:26:36.497Z
card-last-reviewed:: 2022-11-14T16:26:36.497Z
card-last-score:: 3
- Time Multiplex Sharing is when a process is allocated ^^exclusive control of an entire resource for a short period of time^^ (not spatially divisible).
- E.g., the Processor Resource.
- Time Multiplex Sharing is when a process is allocated ^^exclusive control of an entire resource for a short period of time^^ (not spatially divisible).
- What are Resources? #card
card-last-interval:: -1
card-repeats:: 1
card-ease-factor:: 2.46
card-next-schedule:: 2022-11-15T00:00:00.000Z
card-last-reviewed:: 2022-11-14T16:28:34.225Z
card-last-score:: 1
-
Operating Systems
-
OS Organisation
collapsed:: true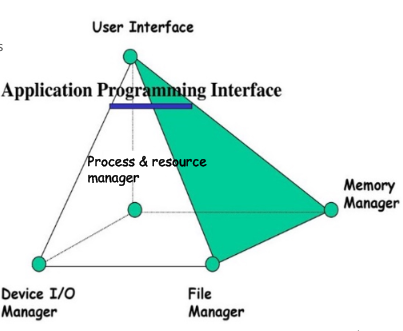
- What is the Process & Resource Manager? #card
card-last-interval:: 0.79
card-repeats:: 2
card-ease-factor:: 2.36
card-next-schedule:: 2022-11-15T10:26:53.305Z
card-last-reviewed:: 2022-11-14T16:26:53.305Z
card-last-score:: 3
- The Process & Resource Manager handles ^^resource allocation.^^
- It uses the abstraction provided by the other managers.
- What is the Memory Manager? #card
card-last-interval:: 4
card-repeats:: 2
card-ease-factor:: 2.22
card-next-schedule:: 2022-11-22T18:34:34.745Z
card-last-reviewed:: 2022-11-18T18:34:34.745Z
card-last-score:: 3
- Besides other functions, the Memory Manager is in charge of the ^^implementation of the virtual memory.^^
- It is classically a separate part of the operating system.
- What does the File Manager do? #card
card-last-score:: 1
card-repeats:: 1
card-next-schedule:: 2022-11-15T00:00:00.000Z
card-last-interval:: -1
card-ease-factor:: 2.6
card-last-reviewed:: 2022-11-14T20:14:20.814Z
- The File Manager abstracts device I/O operations into a relatively simple operation.
- What is the Device Manager? #card
card-last-interval:: -1
card-repeats:: 1
card-ease-factor:: 2.22
card-next-schedule:: 2022-11-15T00:00:00.000Z
card-last-reviewed:: 2022-11-14T16:43:01.202Z
card-last-score:: 1
- The Device Manager handles the details of ^^reading & writing to the physical devices.^^
- The Device Manager is implemented within the device driver.
-
OS Evolution
collapsed:: true-
Computers with no OS
collapsed:: true- Programming in machine language.
- Lack of I/O devices.
-
Rudimentary OS
collapsed:: true- Programming done in Assembly. :LOGBOOK: CLOCK: [2022-09-18 Sun 00:46:32] :END:
- Some basic I/O devices.
- Some I/O control modules - assembler, debugger, loader, linker.
-
Batch Processing System
collapsed:: true- Service a collection of jobs, called a batch, from a queue.
- What is a Job? #card
card-last-interval:: -1
card-repeats:: 1
card-ease-factor:: 2.22
card-next-schedule:: 2022-11-18T00:00:00.000Z
card-last-reviewed:: 2022-11-17T20:19:14.338Z
card-last-score:: 1
- A Job is a predefined sequence of commands, programs, and data combined into a single unit.
- Job Control Language and monitor batch (Interpreter for JCL).
- The user doesn't interact with programs while they operate.
- Process Scheduling: FIFO.
- Memory is divided into two parts: system memory and program memory.
- No special jobs for I/O management, as a job has exclusive access to the I/O devices.
- File management.
-
Operating Systems that use Multiprogramming
collapsed:: true- What is Multiprogramming? #card
card-last-interval:: 4
card-repeats:: 2
card-ease-factor:: 2.22
card-next-schedule:: 2022-11-21T20:25:39.838Z
card-last-reviewed:: 2022-11-17T20:25:39.838Z
card-last-score:: 3
- Mulitprogramming is the technique of loading multiple programs into space-multiplexed memory while time-mulitplexing the processor.
- Timesharing Systems, Real-Time Operating Systems, and Distributed Operating Systems all use multiprogramming.
-
Common Features of Multiprogramming Systems #card
card-last-interval:: 15.05 card-repeats:: 4 card-ease-factor:: 1.94 card-next-schedule:: 2022-11-26T12:30:04.351Z card-last-reviewed:: 2022-11-11T11:30:04.352Z card-last-score:: 3- Multitasking: multiple processes sharing machine resources.
- Hardware Support for memory protection & I/O devices.
- Multi-user & multi-access support (through time-sharing mechanisms).
- Optional support for real-time operations (based on efficient usage of multitasking support).
- Interactive user interface.
-
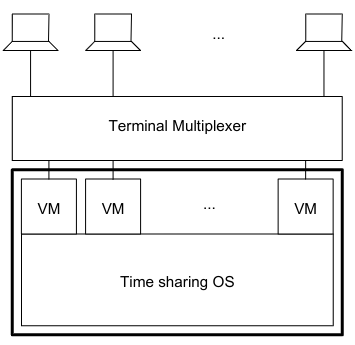
Time Sharing Systems #card
card-last-interval:: 4 card-repeats:: 2 card-ease-factor:: 2.22 card-next-schedule:: 2022-11-18T20:14:17.489Z card-last-reviewed:: 2022-11-14T20:14:17.489Z card-last-score:: 3- Time Sharing Systems have multiprogramming & multi-user support.
- They use time slice (round robin) processor scheduling.
- They have protection & inter-process communication support for Memory Management.
- They have support for the protection & sharing of I/O between users.
- The File Management has protection support & sharing support between users.
-
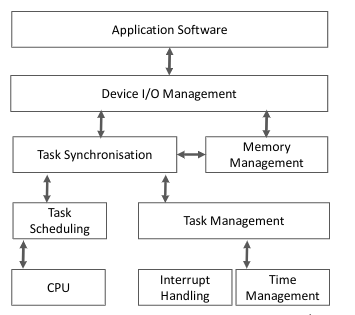
Real-Time Operating Systems #card
card-last-interval:: -1 card-repeats:: 1 card-ease-factor:: 2.6 card-next-schedule:: 2022-11-18T00:00:00.000Z card-last-reviewed:: 2022-11-17T20:16:00.838Z card-last-score:: 1- Real-Time Operating Systems are used whenever a large number of ^^critical external events^^ have to be treated in a short or ^^limited time interval^^ .
- They have support for multiprogramming / multi-tasking.
- The main goal of Real-Time Operating Systems is the minimisation of response time to service the external events.
- Processor Scheduling: Priority-based pre-emptive.
- Memory Management:
- Concurrent processes are loaded into the memory.
- Support for protection & inter-process communication.
- I/O Management:
- Critical in time.
- Processes dealing with I/O are directly connected to the interrupt vectors (for handling interrupt requests).
- File Management:
- File Management may not be present.
- If it exists, it should comply with the requirements for Time Sharing & Real-Time systems.
-
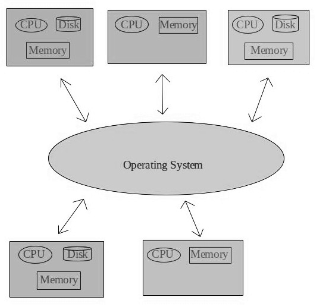
Distributed Operating Systems #card
card-last-interval:: -1 card-repeats:: 1 card-ease-factor:: 2.22 card-next-schedule:: 2022-11-15T00:00:00.000Z card-last-reviewed:: 2022-11-14T20:04:11.371Z card-last-score:: 1- Multiprogramming induces a ^^strong centralisation tendency.^^
- Distributed Operating Systems aim for decentralisation.
- Distributed Operating Systems are based on computer network technologies, with different communication & synchronisation protocols.
- Client-Server application architecture.
- Security & Protection are the primary concerns.
 {:height 313, :width 318}
{:height 313, :width 318}
- What is Multiprogramming? #card
card-last-interval:: 4
card-repeats:: 2
card-ease-factor:: 2.22
card-next-schedule:: 2022-11-21T20:25:39.838Z
card-last-reviewed:: 2022-11-17T20:25:39.838Z
card-last-score:: 3
-
Modern Operating Systems
collapsed:: true- Modern Operating Systems take attributes from Batch, Timesharing, Real-Time, & Distributed Operating Systems.
- Batch OS -> Constant load on the processor on low-priority tasks.
- Timesharing OS -> Interactive processes are treated on a time share.
- Real-Time OS-> Critical Processes (i.e., network drivers) are tread according to real-time constraints.
- Distributed OS -> Client-Server model protocols.
- Modern Operating Systems take attributes from Batch, Timesharing, Real-Time, & Distributed Operating Systems.
-
-
OS Implementation Considerations
collapsed:: true-
Monolithic Operating System #card
collapsed:: true card-last-interval:: 0.85 card-repeats:: 2 card-ease-factor:: 2.36 card-next-schedule:: 2022-11-18T15:50:22.513Z card-last-reviewed:: 2022-11-17T19:50:22.513Z card-last-score:: 3- Monolithic Operating Systems try to achieve the functional requirements by ^^executing all the code in the same address space^^ to increase the performance of the system.
- They are often too complex to manage.
-
Hierarchical Operating System #card
card-last-interval:: -1 card-repeats:: 1 card-ease-factor:: 2.36 card-next-schedule:: 2022-11-18T00:00:00.000Z card-last-reviewed:: 2022-11-17T20:18:29.505Z card-last-score:: 1- Hierarchical Operating Systems run most of their services in the user space, aiming to improve maintainability & modularity of the codebase.
- Suitable for Object-Oriented Programming, the levels are very well-defined.
- Multiprogramming: The illusion that multiple programs are running simultaneously.
- Protection: Access to shared system resources.
- Processor Modes: Different privilege levels.
- Restrictions on the operations that can be run.
- Kernels: Complete control over everything in the system (i.e., supervisor).
-
Multi-Programming #card
card-last-interval:: -1 card-repeats:: 1 card-ease-factor:: 2.32 card-next-schedule:: 2022-11-15T00:00:00.000Z card-last-reviewed:: 2022-11-14T20:23:25.857Z card-last-score:: 1- Multiprogramming is a technique that allows the system to present the illusion that multiple programs are running on the computer simultaneously.
- It is achieved by ^^switching rapidly between programs.^^
- Each program is allowed to execute for a fixed amount of time called a timeslice.
- When a program timeslice ends, the OS stops it, removes it, and gives another program control over the processor - this is a context switch.
- To do a context switch, the OS copies the contents of the current program register file into memory, restores the contents of the next program's register file into the processor, and starts executing the next program.
- From the program POV, they can't tell that a context switch has been performed.
- Protection between multi-programmed programs is very important.
- Many multiprogrammed computers are multi-user - they allow multiple persons to be logged on at a time.
- Besides Protection, data privacy is also important.
-
Protection #card
card-last-interval:: 7.44 card-repeats:: 3 card-ease-factor:: 2.08 card-next-schedule:: 2022-11-22T02:35:46.684Z card-last-reviewed:: 2022-11-14T16:35:46.685Z card-last-score:: 3- The result of any program running on a multiprogrammed computer ^^must be the same^^ as if the program was the only program running on the computer.
- Programs ^^must not be able to access other program's data^^ and must be confident that their data will not be modified by other programs.
- Programs ^^must not interfere with other program's use of I/O devices.^^
- Protection is achieved by having the ^^OS have full control over the resources of the system^^ (processor, memory, & I/O devices).
- Virtual Memory is one of the techniques used to achieve protection between programs.
- Each program operates as if it were the only program on the computer, occupying a full set of the address space as in its virtual space.
- The OS is translating memory addresses that the program references into physical addresses used by the memory system.
- As long two program's addresses are not translated to the same address space, programs can be written as if they were the only ones running on the machine.
- Each program operates as if it were the only program on the computer, occupying a full set of the address space as in its virtual space.
-
Processor Modes
collapsed:: true- What are Processor Modes? #card
card-last-interval:: 4
card-repeats:: 2
card-ease-factor:: 2.32
card-next-schedule:: 2022-11-25T13:06:30.927Z
card-last-reviewed:: 2022-11-21T13:06:30.928Z
card-last-score:: 5
- Processor Modes are operating modes for the CPU that ^^place restrictions^^ on the operations that can be performed by the currently running process.
- Hardware supported CPU modes help the OS to ^^enforce rules^^ that would prevent viruses, spyware, & similar malware from running.
- Only very specific & limited "kernel" code would run unrestricted.
- Any other software (including portions of the OS), would run restricted and would have to ask the "kernel" for permission to modify anything that could compromise the system.
- Multiple mode levels could be designed.
- The mode bit is used to define the execution capability of a program on a processor.
- The mode bit may be logically extended to define areas of memory to be used when the processor is in supervisor mode, versus when it is in user mode.
-
Supervisor Mode #card
card-last-interval:: 31.05 card-repeats:: 4 card-ease-factor:: 2.56 card-next-schedule:: 2022-12-15T21:10:41.635Z card-last-reviewed:: 2022-11-14T20:10:41.635Z card-last-score:: 3- The processor can execute ^^any instruction.^^
- Instructions that can be executed only in supervisor mode are called supervisor, privileged, or protected instructions. (E.g., I/O instructions).
- The executing process has access on both memory spaces.
-
User Mode #card
card-last-interval:: 4 card-repeats:: 2 card-ease-factor:: 2.08 card-next-schedule:: 2022-11-26T13:41:27.100Z card-last-reviewed:: 2022-11-22T13:41:27.101Z card-last-score:: 3- The processor can execute only a ^^subset of the instruction set.^^
- The executing process has access only to the ^^user space.^^
- Some processors do not differentiate between protected mode & user mode.
-
Privileged Mode
- To ensure that the OS is the only one that can control the physical resources, it executes in Privileged Mode.
- The OS is also responsible for Low-Level UI
- When keys are pressed, the OS is responsible to determine which program should receive the input.
- When a program wants to display some output, the user program executes some system call that displays the data.
- User programs execute in User Mode
- When User Mode programs want to execute something that requires privileged rights, it sends a request to the OS, known as a system call, that asks the OS to do the operation for them.
- What are Processor Modes? #card
card-last-interval:: 4
card-repeats:: 2
card-ease-factor:: 2.32
card-next-schedule:: 2022-11-25T13:06:30.927Z
card-last-reviewed:: 2022-11-21T13:06:30.928Z
card-last-score:: 5
-
-
Kernel
collapsed:: true- What is the Kernel? #card
card-last-interval:: 31.36
card-repeats:: 4
card-ease-factor:: 2.8
card-next-schedule:: 2022-12-16T04:09:50.119Z
card-last-reviewed:: 2022-11-14T20:09:50.120Z
card-last-score:: 5
- The Kernel (sometimes called the nucleus) is the part of the operating system that executes in supervisor mode.
- The Kernel operates as trusted software
- It implements protection mechanisms that cannot be changed through the actions of un-trusted software executing in user mode.
- It provides the lowest level abstraction layer for resources (memory, processors, and IO devices).
- A fundamental design decision: Should a given function of the OS be incorporated in the kernel or not?
- Protection issues.
- Performance issues.
- What is the Kernel? #card
card-last-interval:: 31.36
card-repeats:: 4
card-ease-factor:: 2.8
card-next-schedule:: 2022-12-16T04:09:50.119Z
card-last-reviewed:: 2022-11-14T20:09:50.120Z
card-last-score:: 5
-
Methods for Requesting System Services
-
- Through a Command Line Interface
- By calling a specific command.
- Using a command interpreter known as a shell.
-
Command Execution Mechanism #card
card-last-interval:: -1 card-repeats:: 1 card-ease-factor:: 2.5 card-next-schedule:: 2022-11-15T00:00:00.000Z card-last-reviewed:: 2022-11-14T16:27:04.739Z card-last-score:: 1- A key pressed by the user generates a hardware interrupt.
- A specialised module of the OS reads the keyed character and stores it in a special command line buffer.
- There are special characters (e.g., to edit the command line) that are not stored in the command line buffer.
- Control is taken by the shell (command interpreter) when an end of line is detected.
- The command is analysed (with error or success).
- If successful, the shell decides if it is an internal or external command (for another module).
- If internal: the shell tries the execution, which can end successfully or with an error.
- If external: the shell looks for the corresponding executable file & executes it with the detected parameters from the previous phrase.
- A specialised module of the OS reads the keyed character and stores it in a special command line buffer.
- A key pressed by the user generates a hardware interrupt.
-
- From user processes requesting services from the OS
-
System Call
- The parameters of the call are passed according to the specific OS convention & hardware architecture.
- Switch to protected (supervisor) mode using a specific mechanism.
- E.g., software interrupt, trap, special instruction of type "call supervisor".
- This mechanism is different to a normal call.
- A special module takes over, that will analyse the parameters & their access rights.
- This module can reject the system call.
- If accepted, the corresponding routine from the OS is executed and the result is returned to the user.
- Upon return, the user mode is returned.
-
Message
- The user process ^^constructs a message (A) that describes a desired service.^^
- It uses the send function to pass the message to a trusted operating system process.
- The send function checks the message, switches the processor to protected mode, & then delivers the message to the process that implements the target function.
- Meanwhile, the user waits for a result with a message receive operation.
- When the kernel finishes processing the request, it sends a message (B) back to the user process.
-
-